Web Application Firewall (WAF)
The Quant Web Application Firewall has full support for the latest OWASP Core Rule Set, as well as support for integrated Project Honeypot, bot protection, rate limiting, and geo controls.
It may be enabled with granular controls on each domain/route configured to proxy back to your origin server.
Enable WAF
Section titled “Enable WAF”To enable the WAF, simply tick the “Enable WAF” checkbox on any proxy configuration.
Set the WAF to either Report or Block mode to either report on WAF hits or block them.
Use the WAF level slider to change the level of strictness enforced by the WAF. This equates to the ModSecurity Core Rule Set “Paranoia” levels associated with each rule. The default and recommended level is 1.
When enabling the WAF it is recommended you start in Report mode for a period to monitor WAF hits and find and remove false positives through standard browsing behavior. Once you are satisfied you are no longer receiving false positives, move to Block mode.
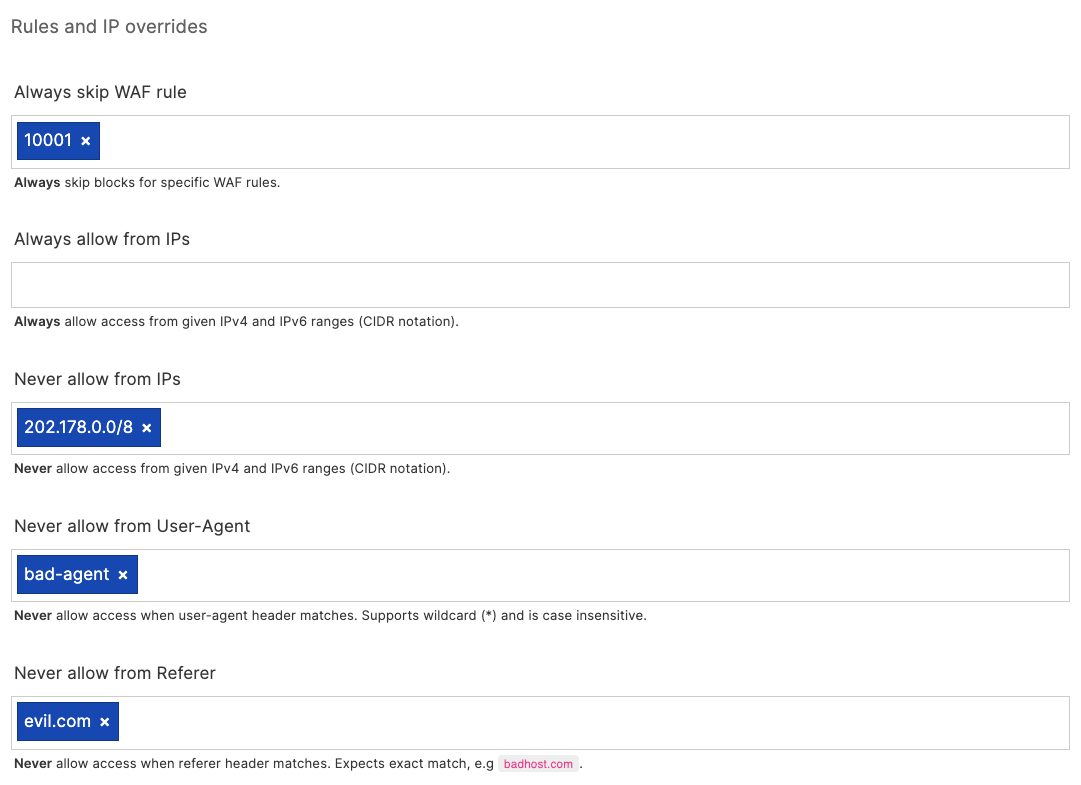
Rules and overrides
Section titled “Rules and overrides”Use the “Rules and overrides” section to disable certain WAF rules, block (or allow) certain IP addresses or ranges, and block based on User-Agent or Referer headers.
Use the “Always allow from IPs” to allow trusted users or networks to bypass the WAF.
Block dictionaries
Section titled “Block dictionaries”Enable block dictionaries to block known bad bots, user-agents, referers and IP addresses associated with bad actors as seen across our network.
Note: We consider these safe to enable, however keep an eye on the WAF hits to ensure you are not inadvertently blocking a crawler or bot you may want to allow. These dictionaries may be overridden if you need further control, contact support for further assistance.
Http:BL (Project Honeypot)
Section titled “Http:BL (Project Honeypot)”If you are a member of Project Honeypot and have a valid API key you may integrate directly with the Http:BL service. From the Http:BL overview page:
Http:BL is a system that allows website administrators to take advantage of the data generated by Project Honey Pot in order to keep suspicious and malicious web robots off their sites. Project Honey Pot tracks harvesters, comment spammers, and other suspicious visitors to websites. Http:BL makes this data available to any member of Project Honey Pot in an easy and efficient way.
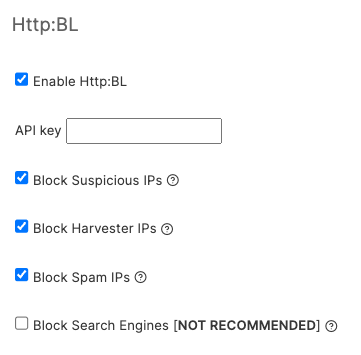
These options protect against known harvesters, bots, spammers and other malicious actors as picked up by the Project Honeypot network of spam traps.
Rate limiting
Section titled “Rate limiting”Rate limiting options are a powerful protection against high traffic events.
IP rate limiting
Section titled “IP rate limiting”IP rate limiting is useful to prevent attacks or excessive traffic from individuals, bots and crawlers. Set the mode to either Report or Enabled to toggle between report and blocking modes.
Next, specify a RPS (requests per second) threshold in seconds, as well as a cool-down period in seconds. The user will be receive a 429: Too Many Requests response during the cool-down period, and this traffic will be kept away from your origin server.
Request header rate limiting
Section titled “Request header rate limiting”You may also use rate limiting grouped by a request header. This can be used on an API service for instance to limit requests by a known group (for example, X-API-Organization), or any other identifier as seen in the request headers.
As with IP rate limiting you may set the RPS threshold and cool-down period to control the traffic.
Custom 403 error pages
Section titled “Custom 403 error pages”When a request is blocked by the WAF you may wish to display a custom 403 page explaining why, and allowing them an avenue to contact you if they feel the block is a false positive.
Create a new static page at the /_quant_waf_403 route. You may wish to use the WYSIWYG or Code editors to do this, see the Content section for more detail.
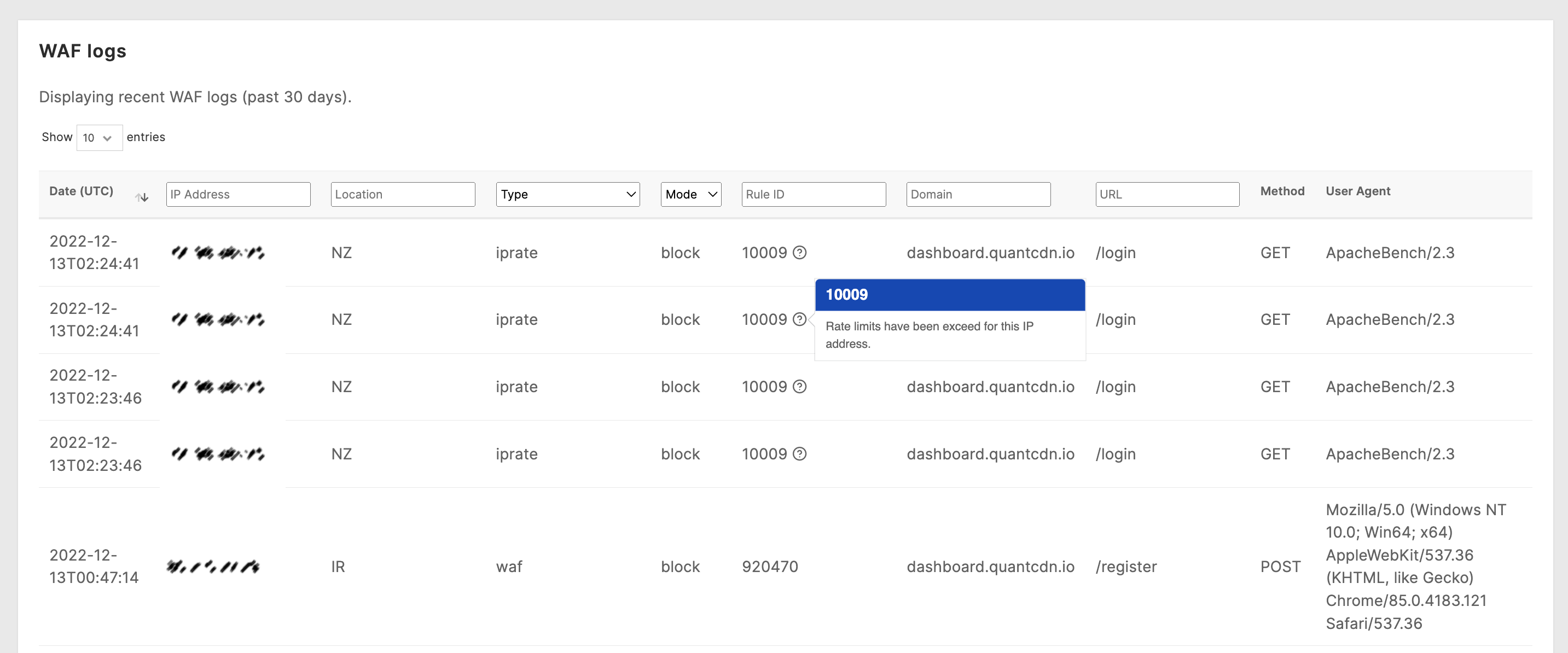
Log viewer
Section titled “Log viewer”The last 30 days of WAF hits are stored and can be viewed directly via the log viewer in the Quant Dashboard.
Navigate to the Security & WAF > WAF Logs section to access the log viewer.
You may optionally filter logs by IP address, Location, Rule type, Mode (Report vs. Block), Rule ID, Domain, and URL.