Improve your security headers
Your website emits headers in each response which are responsible for how clients and browsers interact with your site.
These headers are important as they provide controls which can protect your website from cross site scripting (XSS) and other malicious activity.
We provide an easy way to assess and resolve your security headers directly via the QuantCDN Dashboard. To begin, navigate to the “Security & WAF” > “Headers” section of the Dashboard.
Here, you will see the current state of your security headers.
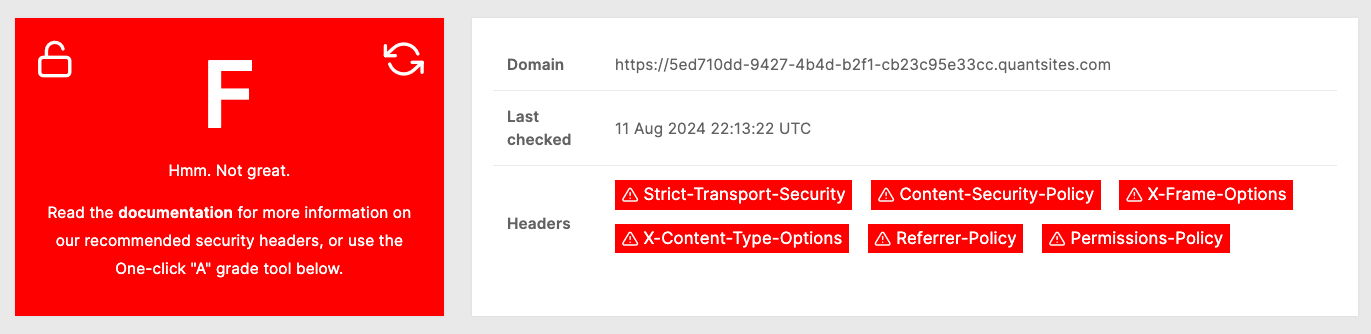
In this example our site is not emiting any values (or insecure values) for the Strict-Transport-Security, Content-Security-Policy, X-Frame-Options, X-Content-Type-Options, Referrer-Policy, and Permissions-Policy headers.
To resolve, we can simply click the “Fix my Security Headers” button to inject some sane default values, which we will describe in detail below. These default values will provide an “A” grade result, which you can also validate via the popular third party tool: Security Headers.
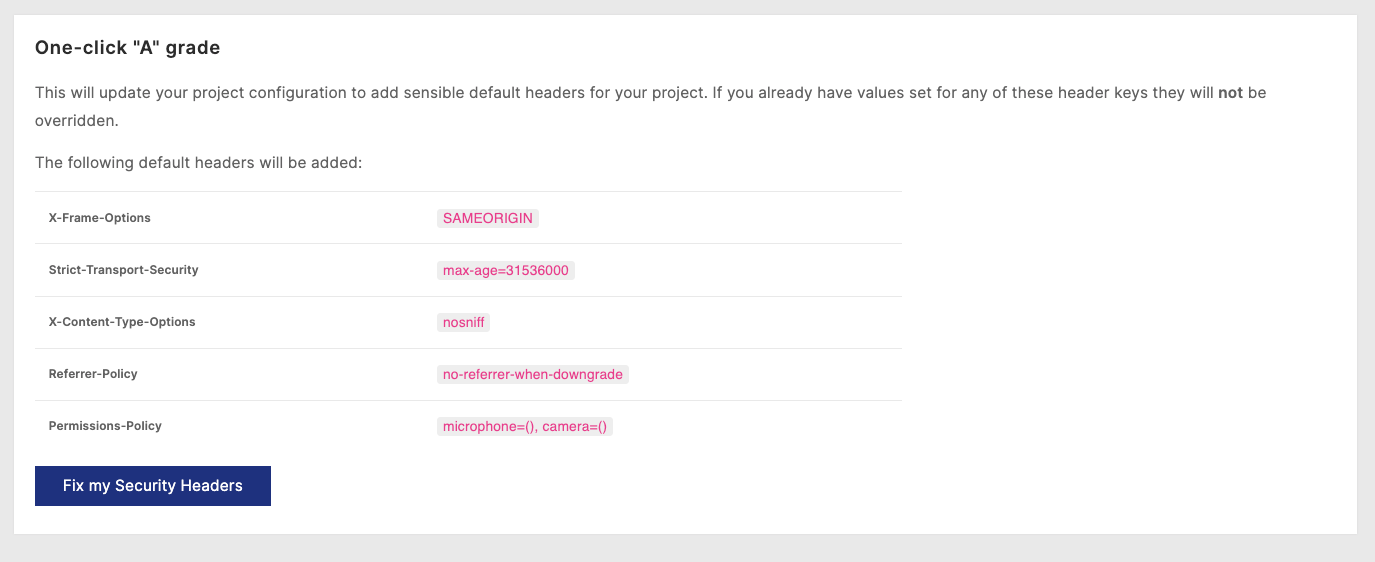
Default values
Section titled “Default values”| Header | Value | Description |
|---|---|---|
| Strict-Transport-Security | max-age=31536000 | A Strict-Transport-Security (STS) header with max-age=31536000 enforces HTTPS for a minimum of 1 year. Quant enforces TLS on all connections, and we will automatically provide SSL certificates. |
| Content-Security-Policy | N/A | We cannot provide default CSP values as they are site specific. |
| X-Frame-Options | SAMEORIGIN | The X-Frame-Options header with a value of SAMEORIGIN tells browsers that this page should only be framed (i.e., loaded within an iframe) if the request originated from the same domain as the current page. |
| X-Content-Type-Options | nosniff | The X-Content-Type-Options header with a value of nosniff tells browsers not to MIME-sniff the content type, and instead rely on the Content-Type HTTP header for determining the actual type of the response. |
| Referrer-Policy | no-referrer-when-downgrade | The Referrer-Policy header with a value of no-referrer-when-downgrade tells browsers to not send any referrer information when an HTTPS page is loaded from an HTTP link. This prevents referrer leakage in cases where the protocol is downgraded. |
| Permissions-Policy | microphone=(), camera=() | The Permissions-Policy header with a value of microphone=(), camera=() indicates that the website has explicitly denied access to the user’s microphone and camera, even if the site would normally request permission for these features. This is an example of a “deny” policy for specific permissions. If your website requires microphone or camera access you may reconsider these values. |
For more detail on each of these headers refer to the section below.
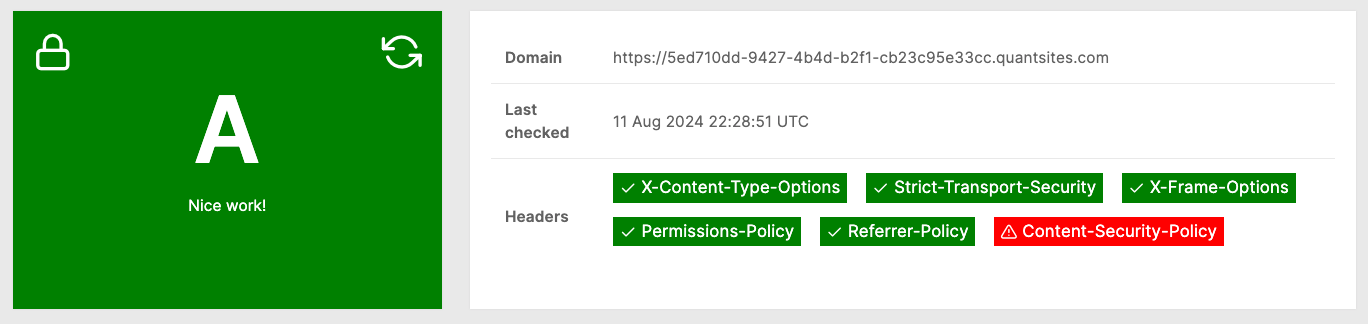
After these values are set, you can click the “refresh” icon to re-assess your security headers. At this point you should see an “A” grade as expected.
Security headers detail
Section titled “Security headers detail”| Header | Description |
|---|---|
| Strict-Transport-Security | The Strict-Transport-Security (STS) HTTP header is used to enforce secure connections, preventing downgrade attacks and ensuring all communications between a client and server are encrypted. It ensures that a connection cannot be downgraded to an insecure protocol, such as HTTP instead of HTTPS. |
| Content-Security-Policy | The Content-Security-Policy (CSP) HTTP header is used to define which sources of content are allowed to be executed within a web page, helping protect against XSS attacks by specifying which scripts or resources can be loaded. It allows developers to set rules on where resources like scripts, stylesheets, and fonts can be loaded from. |
| X-Frame-Options | The X-Frame-Options HTTP header is used to prevent clickjacking attacks by controlling whether a page can be loaded within an iframe on another domain, or if it should not be framed at all. It allows developers to specify which domains are allowed to frame their content. (Note: The X-Frame-Options has been deprecated and replaced with the Content-Security-Policy (CSP) header’s “frame-ancestors” directive in modern browsers.) |
| X-Content-Type-Options | The X-Content-Type-Options HTTP header is used to prevent MIME-sniffing attacks by indicating that the server will always provide a specific Content-Type, preventing the browser from attempting to sniff and change it. This helps prevent attacks where an attacker might try to manipulate the browser’s interpretation of content based on its type. |
| Referrer-Policy | The Referrer-Policy HTTP header is used to control whether or how the Referer (sic) HTTP header is sent with requests from a client to a server, protecting user privacy and preventing leaks of sensitive information such as referrers. It allows developers to set policies on what data about the previous page can be shared with the current page’s server. |
| Permissions-Policy | The Permissions-Policy HTTP header is used to declare which permissions (such as camera, microphone, or geolocation) a website requires, allowing users to make informed decisions about which permissions are necessary and granting them control over their data. It helps protect user privacy by providing transparency into what permissions a site needs to function. |
